The significance of HIPAA compliance for medical providers cannot be overstated.

In 2023, 37% of healthcare organizations lacked a comprehensive IT security plan (HIPAA Journal).
A data breach response plan should integrate IT security measures for medical data protection & follow best practices for incident response in healthcare.
This includes developing a cyber incident response strategy that prioritizes network security healthcare.
Effective compliance management ensures adherence to HIPAA breach notification requirements, crucial for managing compliance in healthcare organizations.
The Office for Civil Rights resolved 97% of HIPAA complaints through corrective actions (Healthcare Compliance Pros).
Understanding how to develop a HIPAA-compliant breach response plan is essential.
Such plans protect patient trust & the organization’s reputation.
By developing a cyber incident response plan for healthcare, providers can proactively–address vulnerabilities & enhance data security.
Understanding HIPAA & Breach Response Requirements
Ensuring HIPAA compliance is fundamental for medical providers to protect patient data & maintain trust.
A critical aspect of this compliance is having a comprehensive incident response plan that aligns with HIPAA breach notification requirements.
We’ll outline the key components & requirements of the HIPAA Breach Notification Rule, essential for any cyber incident response strategy.
Key Components of the HIPAA Breach Notification Rule
The HIPAA Breach Notification Rule mandates that covered entities and their business associates must provide notification following a breach of unsecured protected health information (PHI).
This requirement includes notifying affected individuals, regulatory bodies, and the media for breaches involving more than 500 records.

Notification Requirements for Breaches Involving 500+ Records
When a breach affects more than 500 individuals, additional notification requirements come into play.

Essential Components of an Incident Response Plan
Developing a robust incident response plan involves several key elements to ensure an effective response to data breaches.

Incorporating these components into an incident response plan not only ensures compliance with HIPAA but also strengthens overall compliance management & network security healthcare.
For instance, having a detailed IT security plan and clear protocols for data breach mitigation can significantly–reduce the impact of a breach.
According to a 2023 report, organizations with a well-defined incident response plan can reduce the cost of a data breach by up to 54% (HIPAA Journal) (HIPAA Journal).
Developing a Comprehensive Breach Response Plan
A comprehensive incident response plan is essential for maintaining HIPAA compliance, protecting patient data.
Preparing for potential breaches involves regular risk assessments, continuous monitoring, and updating security measures.
Early detection of breaches & swift identification of their source and scope are crucial for effective data breach mitigation.
We’ll detail the steps & best practices for developing a cyber incident response plan for healthcare.
Importance of Risk Assessments & Employee Training
Regular risk assessments are a cornerstone of compliance management.
They help identify vulnerabilities & areas needing improvement.
Employee training ensures staff are aware of their roles in maintaining IT security measures for medical data protection.
- Conduct thorough risk assessments annually.
- Train employees on data security protocols and HIPAA breach notification requirements.
- Implement simulated breach scenarios to test employee response.
- Update training materials regularly to reflect new threats and best practices for incident response in healthcare.
- Encourage a culture of security awareness among staff.
Continuous Monitoring and Updating Security Measures
Network security healthcare requires continuous monitoring to detect potential threats early.
Updating security measures regularly is vital to stay ahead of cyber threats.
- Use Security Information and Event Management (SIEM) systems for real-time monitoring.
- Regularly update antivirus and firewall protections.
- Implement multi-factor authentication for all systems accessing PHI.
- Schedule periodic security audits to assess the effectiveness of current measures.
- Ensure all software and hardware are updated with the latest security patches.
Methods for Early Detection of Breaches
Early detection is critical in limiting the damage caused by a breach.
Employing robust detection methods can help quickly identify & address security incidents.
- Utilize SIEM systems to collect and analyze security data.
- Implement intrusion detection systems (IDS) to monitor network traffic for suspicious activity.
- Encourage employees to report any unusual activities or potential breaches immediately.
- Conduct regular network scans to identify vulnerabilities.
- Develop a clear protocol for incident reporting and escalation.
Identifying the Source & Scope of a Breach
Quickly identifying the source and scope of a breach is essential for effective data breach response and mitigation.
- Isolate affected systems immediately to prevent further data loss.
- Use forensic tools to analyze and trace the breach’s origin.
- Document all findings and actions taken during the investigation.
- Communicate findings with relevant stakeholders, including legal and compliance teams.
- Develop a remediation plan based on the breach’s severity and impact.
A robust incident response plan is not just about meeting regulatory requirements but also about protecting patient trust and the organization’s reputation.
For example, a well-defined plan can reduce the cost of a data breach by up to 54% (HIPAA Journal) (Healthcare Compliance Pros).
By incorporating these elements, medical providers can ensure comprehensive HIPAA compliance & data security.
Mitigating the Impact of a Breach
Mitigating the impact of a data breach involves swift, decisive actions to contain both cyber & human-caused leaks.
Immediate steps are crucial to prevent further data loss & maintain HIPAA compliance.
Let’s outline procedures for containment, highlight the importance of immediate actions, and provide a detailed communication plan to notify all stakeholders.
Containment Procedures for Cyber & Human-caused Data Leaks
Effective data breach response begins with containment.
This involves isolating compromised systems, removing threats such as malware.
- Isolate Affected Systems: Disconnect compromised systems from the network to prevent further spread.
- Remove Malware: Utilize anti-malware tools to eliminate malicious software.
- Secure Backup Data: Ensure backup data is intact and secure to facilitate recovery.
- Block Unauthorized Access: Update firewalls and access controls to block intrusions.
- Monitor for Further Threats: Continuously monitor systems to detect additional threats.
Importance of Immediate Actions
Taking immediate action is vital for data breach mitigation.
Rapid response minimizes damage, ensuring regulatory compliance.
- Limit Data Loss: Quick isolation of breaches limits the amount of data compromised.
- Reduce Downtime: Swift action reduces system downtime, maintaining operational continuity.
- Protect Patient Trust: Immediate response helps maintain patient trust and confidence.
- Comply with Regulations: Adhering to HIPAA breach notification requirements within specified timelines is mandatory.
- Mitigate Financial Impact: Early containment can significantly reduce the financial costs associated with data breaches.
Communication Plan for Notifying Stakeholders
A well-structured communication plan is essential for effective breach management.
Notifications should comply with HIPAA breach notification standards & state laws.
- Identify Affected Individuals: Determine the individuals whose data has been compromised.
- Prepare Notification Content: Include details about the breach, steps taken to mitigate damage, and recommendations for personal data protection.
- Notify Regulatory Bodies: Report the breach to the Office for Civil Rights (OCR) within 60 days if more than 500 records are affected (Healthcare Compliance Pros).
- Engage Law Enforcement: Notify local or federal law enforcement agencies if criminal activity is suspected.
- Issue Media Statements: Release information to the media if required by the scale of the breach.
Callnovo Contact Center’s HIPAA-compliant Solutions

With extensive experience in the industry, Callnovo offers tailored outsourcing solutions that address the unique needs of healthcare organizations, ensuring that patient data remains secure and providers maintain compliance with all relevant regulations.
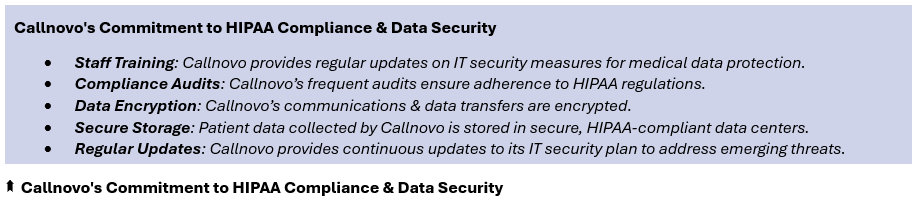
Callnovo’s Commitment to HIPAA Compliance & Data Security
Callnovo’s commitment to HIPAA compliance is evident in its rigorous adherence to security protocols and standards.
Callnovo ensures all staff are trained in HIPAA breach notification requirements, equipped with the knowledge to handle sensitive patient information securely.
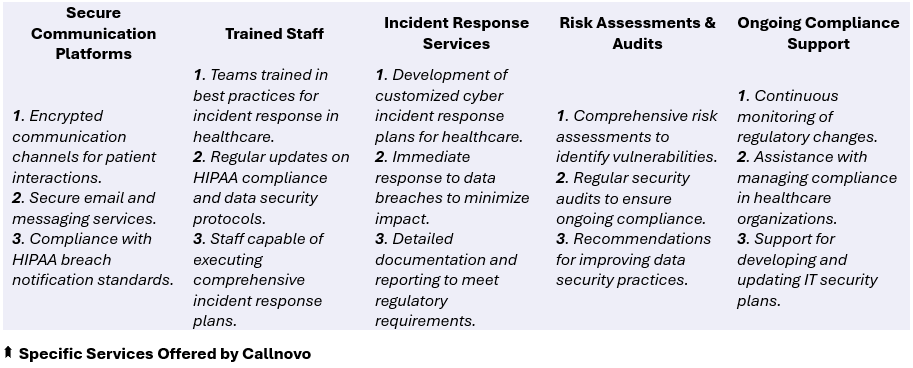
Specific Services Offered by Callnovo
Callnovo offers a range of services designed to support healthcare providers in managing their compliance management and cyber incident response needs.
These services ensure robust network security healthcare & effective data breach mitigation.


Conclusion
A robust incident response plan is critical for ensuring HIPAA compliance & safeguarding patient data.
Medical providers must prioritize data breach mitigation, adhering to HIPAA breach notification requirements to maintain trust & avoid severe penalties.
By implementing best practices, continually–updating IT security measures for medical data protection, providers can effectively–manage compliance and respond swiftly to incidents.

Callnovo’s expertise in developing HIPAA-compliant breach response plans and their commitment to data security provide medical providers with the assurance that their sensitive data is protected.
Choosing Callnovo Contact Center allows medical providers to focus on delivering quality patient care while ensuring regulatory compliance.
By leveraging Callnovo’s solutions, healthcare organizations can foster long-term trust & confidence, reinforcing their reputation, ensuring the security of patient data.
Emphasizing the importance of an effective cyber incident response strategy, Callnovo stands as a reliable partner in managing compliance in healthcare organizations.

